Advanced technologies are both good for consumers and harm if hacked by hackers. This is a problem that will only get worse in the future, because many companies underestimate or completely ignore cybersecurity. Any thing with a microchip can be hacked.
Here 7 unusual things hackers can hack.
7. Implants
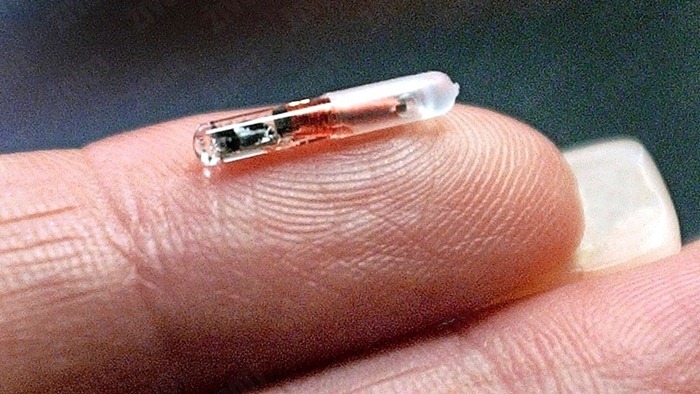 Any medical device in a human body and connected to the Internet is vulnerable to hackers. In 2011, at the Black Hat computer security event, researcher Jerome Radcliffe demonstrated the vulnerability of his insulin pump by hacking it. It could raise or lower the insulin dose to dangerous or even lethal levels, and the device would not warn the user about it.
Any medical device in a human body and connected to the Internet is vulnerable to hackers. In 2011, at the Black Hat computer security event, researcher Jerome Radcliffe demonstrated the vulnerability of his insulin pump by hacking it. It could raise or lower the insulin dose to dangerous or even lethal levels, and the device would not warn the user about it.
6. Toilets
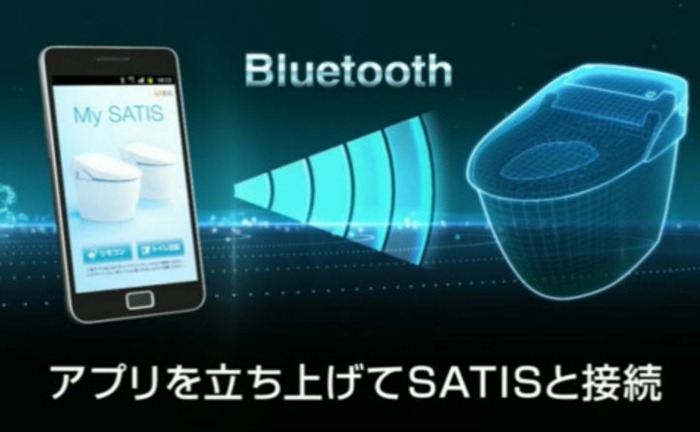 Even the restroom cannot be escaped from hackers. This applies to those in whose homes a Japanese toilet innovation called Satis is installed. These smart toilets are monitored by a smartphone app called My Satis. It uses a single Bluetooth PIN for every toilet. How can an attacker who hacked My Satis annoy the user? For example, to force the toilet to constantly flush water, and this is an additional cost when paying by the meter. And also turn on the air purifier, close and lower the toilet lid, and do not turn off the built-in sound module, which "covers" the sounds of bowel emptying.
Even the restroom cannot be escaped from hackers. This applies to those in whose homes a Japanese toilet innovation called Satis is installed. These smart toilets are monitored by a smartphone app called My Satis. It uses a single Bluetooth PIN for every toilet. How can an attacker who hacked My Satis annoy the user? For example, to force the toilet to constantly flush water, and this is an additional cost when paying by the meter. And also turn on the air purifier, close and lower the toilet lid, and do not turn off the built-in sound module, which "covers" the sounds of bowel emptying.
5. Emergency notification system
 Another unusual thing that can be hacked by hackers. In 2014, an emergency warning system in Montana warned viewers that "the dead come out of their graves and attack the living." Subsequently, the TV channel apologized to the townspeople, explaining that the message appeared as a result of hacking into the emergency notification system. Similar pranks have occurred in other American states, and one of them - during the broadcast of the children's show "Barney and Friends". And although the entertainment of "computer pests" did not harm anyone, this does not mean that subsequent alerts will be just as harmless.
Another unusual thing that can be hacked by hackers. In 2014, an emergency warning system in Montana warned viewers that "the dead come out of their graves and attack the living." Subsequently, the TV channel apologized to the townspeople, explaining that the message appeared as a result of hacking into the emergency notification system. Similar pranks have occurred in other American states, and one of them - during the broadcast of the children's show "Barney and Friends". And although the entertainment of "computer pests" did not harm anyone, this does not mean that subsequent alerts will be just as harmless.
4. "Smart" houses
 In 2015, an experiment was conducted in the West on the vulnerability of smart home automation devices. Of the 16 devices, only one was difficult to break into.
In 2015, an experiment was conducted in the West on the vulnerability of smart home automation devices. Of the 16 devices, only one was difficult to break into.
3. Aircraft
 To find a hacker loophole in airplanes, one researcher purchased genuine parts from an aircraft equipment supplier to simulate the exchange of data between a passenger plane and an air traffic controller. He showed that aircraft safety is so weak that a mobile device with a DIY application can access various aircraft systems. Terrorists don't even need to carry weapons aboard an airliner if they can take control of the steering and direct the winged vehicle to the desired target.
To find a hacker loophole in airplanes, one researcher purchased genuine parts from an aircraft equipment supplier to simulate the exchange of data between a passenger plane and an air traffic controller. He showed that aircraft safety is so weak that a mobile device with a DIY application can access various aircraft systems. Terrorists don't even need to carry weapons aboard an airliner if they can take control of the steering and direct the winged vehicle to the desired target.
2. Vehicle
 In 2015, researchers used a zero-day exploit targeting the Jeep Cherokee to wirelessly control the car.The jeep driver, a reporter who participated in the experiment, was driving along the highway at a speed of 115 kilometers per hour, when the authors of the experiment set the cooling to maximum, changed the radio station, turned on the windshield wiper? And displayed the message “You are doomed!” On the digital display. The driver tried to manually stop these outrages, but to no avail. Although he knew in advance what would happen, he still experienced several unpleasant moments. The researchers warn that these are only "flowers". They could suddenly stop the car, which would lead to an accident.
In 2015, researchers used a zero-day exploit targeting the Jeep Cherokee to wirelessly control the car.The jeep driver, a reporter who participated in the experiment, was driving along the highway at a speed of 115 kilometers per hour, when the authors of the experiment set the cooling to maximum, changed the radio station, turned on the windshield wiper? And displayed the message “You are doomed!” On the digital display. The driver tried to manually stop these outrages, but to no avail. Although he knew in advance what would happen, he still experienced several unpleasant moments. The researchers warn that these are only "flowers". They could suddenly stop the car, which would lead to an accident.
1. New computer
 A new computer that is not connected to the Internet ranks first in high-tech things that are vulnerable to hacker attacks. Some Chinese PCs were sold with a virus preinstalled to spy on users and prevent them from working antivirus... Microsoft's investigation revealed that computers were infected with Nitol malware. It spread via removable media and managed to infect millions of computers across China.
A new computer that is not connected to the Internet ranks first in high-tech things that are vulnerable to hacker attacks. Some Chinese PCs were sold with a virus preinstalled to spy on users and prevent them from working antivirus... Microsoft's investigation revealed that computers were infected with Nitol malware. It spread via removable media and managed to infect millions of computers across China.

